Microsoft Defender XDR Lab Environment
Author: Matthew Ramos
Environment Type: Homelab (Test Environment)
Tools Used: Microsoft Defender for Endpoint, Microsoft 365 Defender, Microsoft Entra ID, Intune, Windows 11 VM
Objective
Build and evaluate a Microsoft Defender XDR lab to simulate enterprise security posture, including endpoint threat detection, automated response, incident correlation, and integration with identity and device management tools. The goal was to test Defender’s full capabilities across detection, prevention, and remediation scenarios.
Implementation Breakdown
1. Device Onboarding & Baseline Setup
- Provisioned Windows 11 VM and enrolled it via Intune.
- Device joined to Entra ID and placed in the test security group.
- Onboarded to Microsoft Defender for Endpoint using Intune configuration profiles.
- Verified sensor communication and policy deployment.
2. Security Configuration in Intune
- Configured endpoint security policies in Intune:
- Antivirus (Defender AV, Cloud-delivered protection)
- Endpoint Detection & Response (EDR)
- Attack surface reduction rules
- Web content filtering
- Assigned policies to the test group and confirmed enforcement via Defender Security Center.
3. Threat Simulation & Detection
- Ran controlled malware simulations (e.g., EICAR test files).
- Triggered alerts for file-based threats, suspicious PowerShell activity.
- Confirmed detections in Microsoft 365 Defender portal.
- Observed automatic alert correlation and incident creation.
4. Incident Response Testing
- Used Microsoft 365 Defender to triage incident:
- Mapped alerts to MITRE ATT&CK tactics
- Viewed device timeline and automated investigation
- Enabled automated response actions (e.g., isolate device, collect investigation package).
- Verified remediation actions were successful and audit-logged.
Automation Highlights
- Alerts were correlated into incidents using Defender’s XDR engine.
- Auto-remediation workflows triggered based on severity and device group.
- Integrated with Microsoft Entra ID and Intune for context-based decisions.
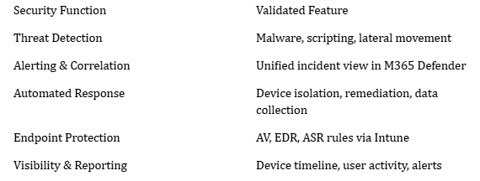
Security Validation
Lessons Learned / Next Steps
- Defender XDR effectively correlates multi-layer alerts into actionable incidents.
- Future plan: Connect lab to Azure Sentinel for extended detection & response (XDR + SIEM).
- Expand device types (macOS, Android) and test mobile threat defense.